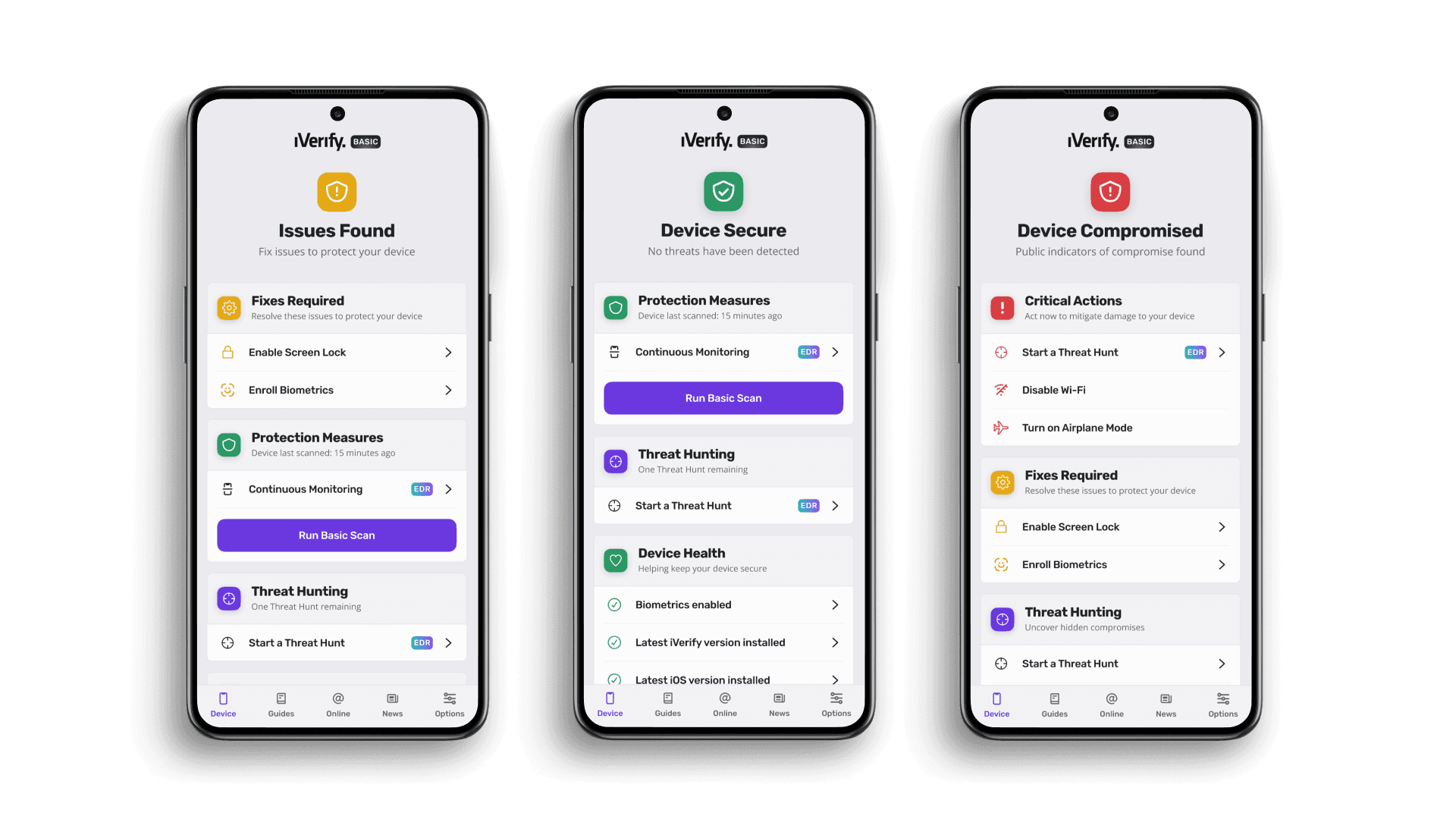
Respect user privacy and protect the enterprise
iVerify's iOS and Android apps provide the protection necessary for users to access corporate applications while eliminating the need to sniff through users private data. When a threat is detected users are notified and can access security guides to understand how to stay safe.






Protect every phone from the actual threats they face
Guard against smishing, social engineering, credential theft, account takeover, spyware, sophisticated malware and zero-day vulnerabilities.
Secure all devices with access to corporate data, no MDM required
Manage and restrict access to critical company resources like email, slack, and cloud data with easy-to-configure policies and Integrations with Okta and Azure.
iVerify's Privacy-Focused Security Protects Figma's People-First Environment
Figma faced a complex balancing act: they needed better visibility and control over its BYOD environment while maintaining its commitment to employee privacy and choice.
Figma choose iVerify for their robust protection against spyware and zero-day attacks, while prioritizing user privacy by strictly avoiding PII collection or uploading sensitive telemetry data.

iVerify Enterprise offers real-time threat detection and response optimized for mobile architectures, enabling rapid mitigation of threats while minimizing device and user disruption across BYOD and managed device fleets.
Unrivaled Mobile Threat Hunting
Secure All BYOD & Managed Devices
Privacy-Centric Security by Design
Optimized Performance & Rapid Deployment