Blog
Meet Cellik - A New Android RAT With Play Store Integration
Daniel Kelley, iVerify Research Fellow
Dec 16, 2025

Cellik is a newly identified Android RAT that offers full device control and real-time surveillance, with Play Store integration that lets attackers bundle it into legitimate apps.
Discovered via cybercrime networks, Cellik comes packed with capabilities previously seen only in advanced spyware: real-time screen streaming, keylogging, remote camera/microphone access, hidden web browsing, notification interception, and even an app-injection system for stealing data from other apps.
Uniquely, Cellik integrates with Google Play Store apps and includes a one-click APK builder, allowing attackers to wrap its payload inside legitimate apps for stealthy, widespread deployment.
Full Device Control and Live Monitoring
Once installed on a target phone, Cellik gives its operator complete control over the device. It can stream the screen in real time and even remotely control the UI, essentially acting like an invisible VNC session on the phone. This means an attacker can watch the victim’s screen live with minimal lag and simulate taps or swipes as if holding the device.

Figure 1. Cellik live screen streaming/remote control view from the operator panel.
All on-screen notifications can be intercepted as well - the RAT pulls in the full notification history and live alerts from any app, allowing the operator to read private messages or one-time passcodes that appear on the victim’s device.

Figure 2. Live keylogger module in the Cellik control panel.
Beyond screen and keyboard surveillance, Cellik has full file system access. The controller can browse through all files on the device, download or upload files, delete data, and even access cloud storage directories linked to the phone. All file transfers and exfiltration are done with encryption to avoid detection.

Figure 3. Cellik RAT file manager module (context menu open on a client).
Hidden Browser and Injection Attacks
Cellik also enables active web-abuse and phishing on the infected device. It contains a hidden browser module that runs an invisible web browser instance on the phone.
The attacker can remotely navigate to websites, click links, and fill out forms through this hidden browser, all without the phone’s owner seeing any activity on their screen. This feature streams screenshots back to the attacker in real time, essentially giving a live feed of any page the attacker visits.
Using the hidden browser, a cybercriminal could quietly log into websites using the victim’s saved cookies, or auto-fill credentials on phishing pages. Cellik can capture any form data submitted in the hidden browser, so if the victim is tricked into entering passwords or credit card info, the RAT will intercept those details.

Figure 4. Hidden browser module interface used for stealth browsing/phishing.
Another feature is Cellik’s injection system. This toolkit lets the attacker inject malicious overlays or code into other apps on the device. In practice, this could mean pushing fake login screens on top of banking apps or intercepting data from within other applications. Cellik’s control panel allows the operator to manage active injections, monitor their status, and collect any data harvested from them.

Figure 5. Cellik RAT’s advertised “advanced injection system” features list.
The RAT comes with an “injector lab” to create custom injection templates and supports multiple simultaneous injections across different apps. For example, an attacker could enable a Facebook overlay phish and a Gmail overlay phish at the same time, and the RAT would feed credentials from both back to the command center.
Google Play Store Integration and Custom APK Generation
One of Cellik’s most problematic features is its integration with Google Play and an automated APK builder for malware distribution. Through its control interface, an attacker can browse the entire Google Play Store catalogue and select legitimate apps to bundle with the Cellik payload. With one click, Cellik will generate a new malicious APK that wraps the RAT inside the chosen legitimate app.
This means a cybercriminal can take a popular app (like a game or utility that targets are likely to install), insert Cellik’s code into it, and repackage it as an installer, all using Cellik’s built-in toolkit.

Figure 6. Cellik RAT’s feature list for “play store integration & APK builder”.
The seller claims Cellik can bypass Google Play security features by wrapping its payload in trusted apps, essentially disabling Play Protect detection. While Google Play Protect typically flags unknown or malicious apps, trojans hidden inside popular app packages might slip past automated reviews or device-level scanners.
A Growing Trend in Android MaaS (Malware-as-a-Service)
Cellik is not an isolated case but part of a larger trend of turnkey Android malware platforms. As noted in our earlier analysis of HyperRat, the Android malware-as-a-service market has matured, even low-skilled attackers can now run mobile spyware campaigns with minimal effort.
Providers on underground forums offer subscription-based RATs that handle everything from the malicious APK generation to cloud C2 infrastructure. Cellik’s feature set is reminiscent of HyperRat and other kits like PhantomOS and Nebula, all of which bundle silent app installation, credential theft, and remote control into user-friendly dashboards.
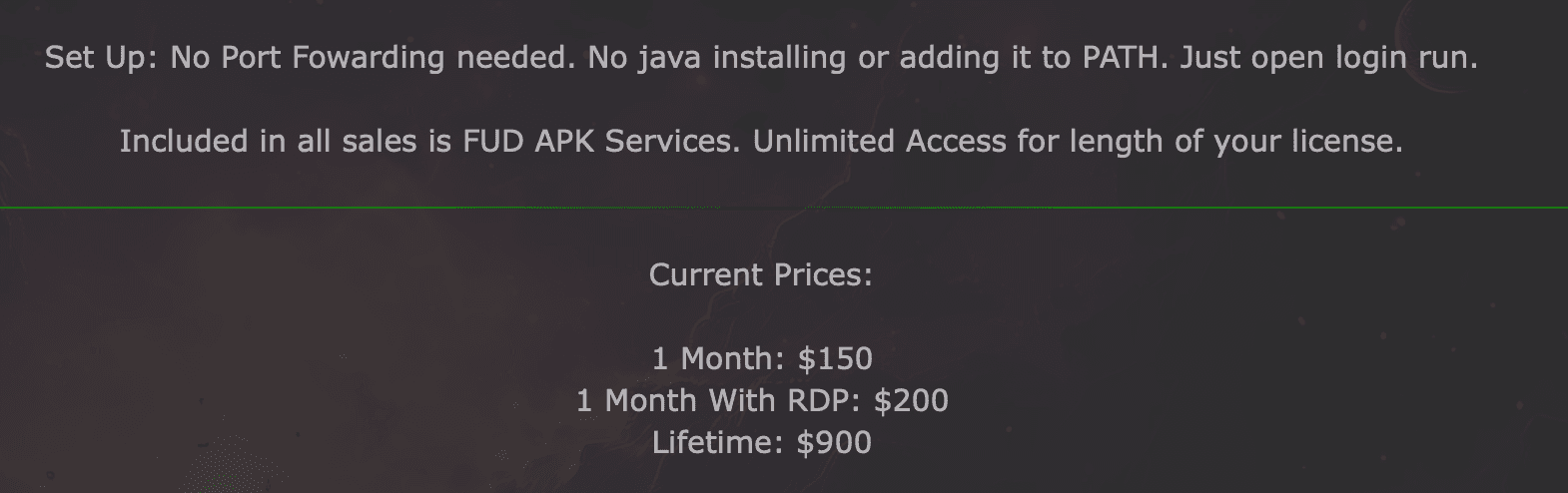
What sets Cellik apart is its Play Store app integration and the sheer breadth of its capabilities for the price point. Those features include advanced location tracking, real-time multimedia capture, communications surveillance, crypto-wallet theft, and even AI driven analysis of user behavior.
Take Your Next Steps With iVerify
Cellik RAT is a good reminder that Android malware is not just for elite cybercriminals anymore. These kits are packaged, sold, and ready for anyone to deploy.
That is exactly why iVerify Threat Intelligence tracks new mobile threats like HyperRat, PhantomOS, and Nebula the moment they surface on underground networks, then turns what we learn into practical indicators and on-device detections your team can use right away.
The goal is simple: help you spot mobile attacks early, understand how they work, and stop them before they spread. If you want to see what this looks like in the real world, book a quick demo and we will walk you through Threat Intelligence and what it can uncover in your environment.
Get Our Latest Blog Posts Delivered Straight to Your Inbox
Subscribe to our blog to receive the latest research and industry trends delivered straight to your inbox. Our blog content covers sophisticated mobile threats, unpatched vulnerabilities, smishing, and the latest industry news to keep you informed and secure.



